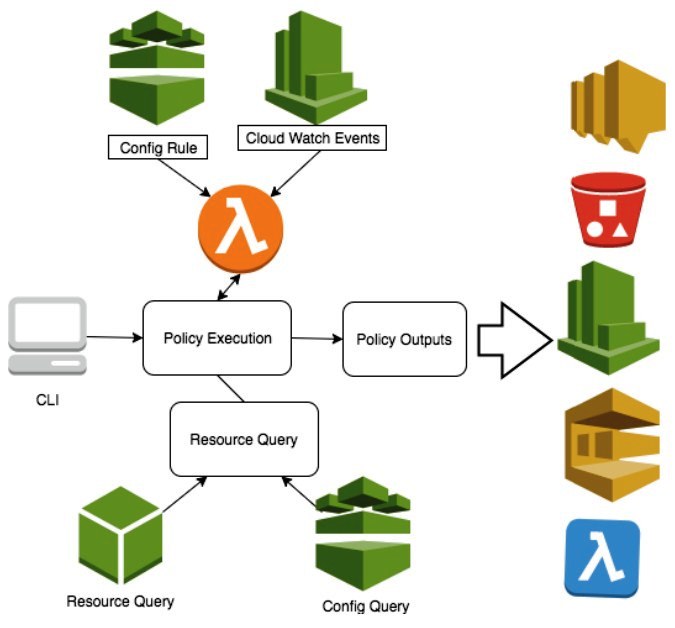
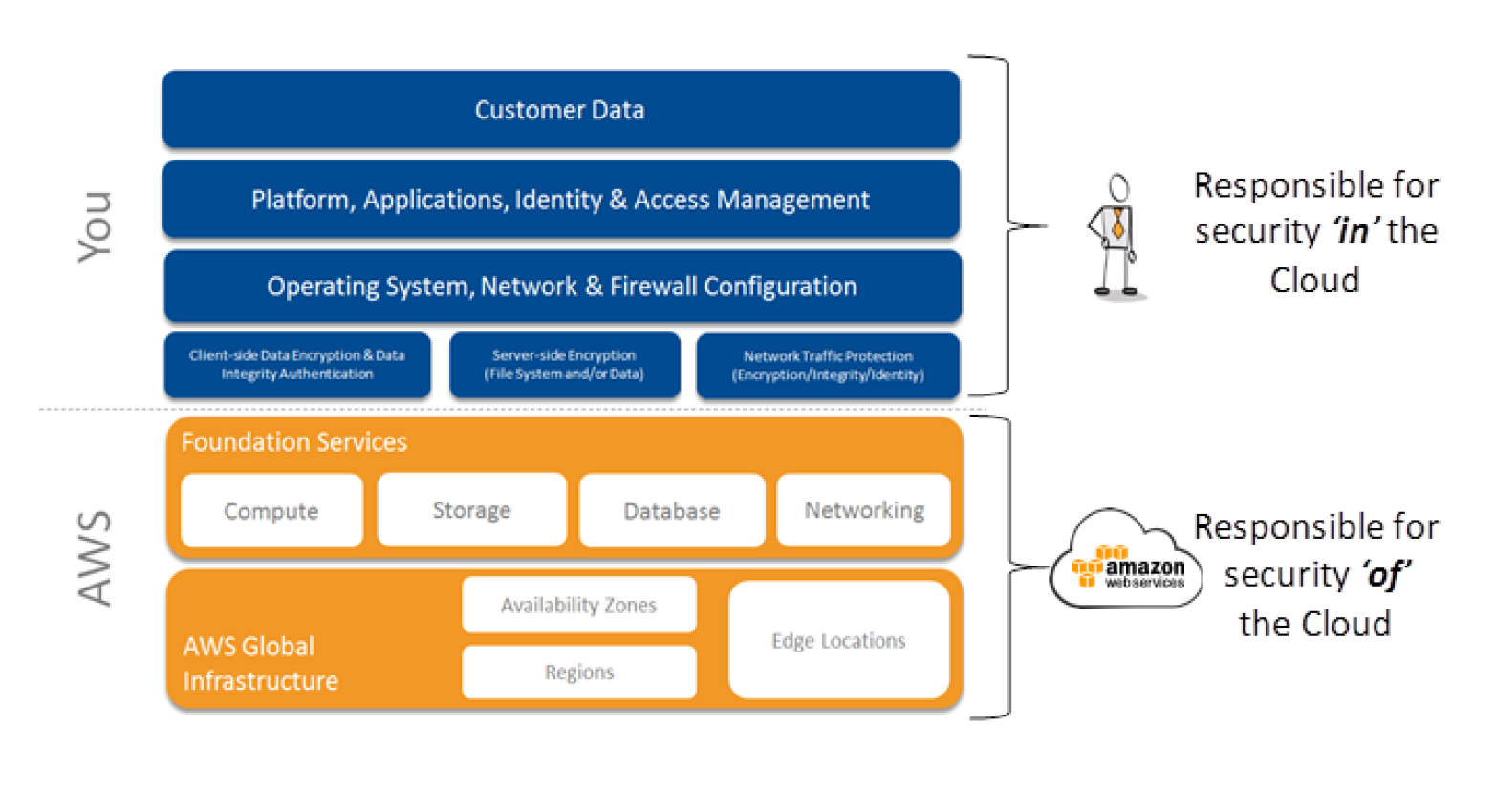
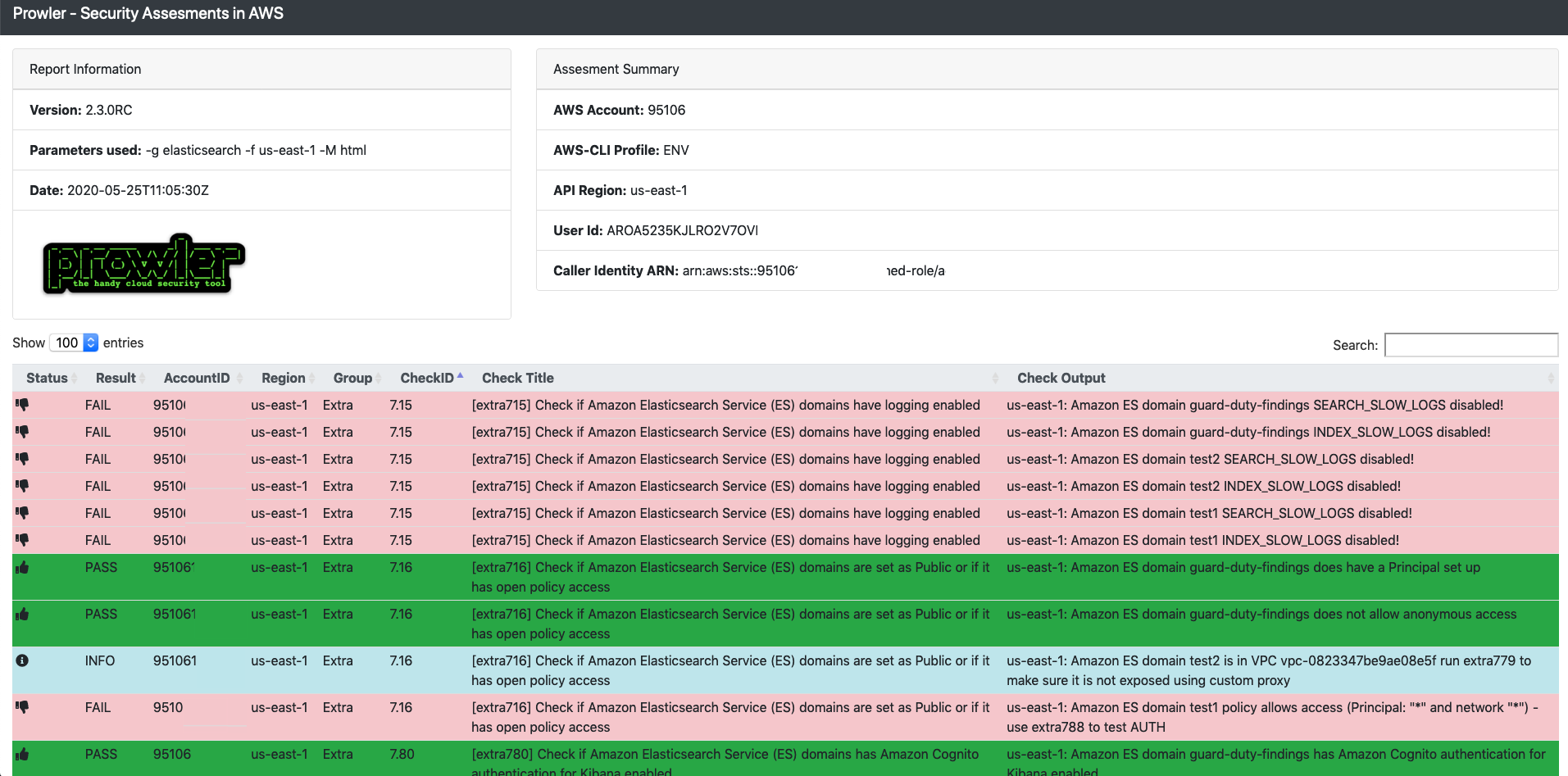
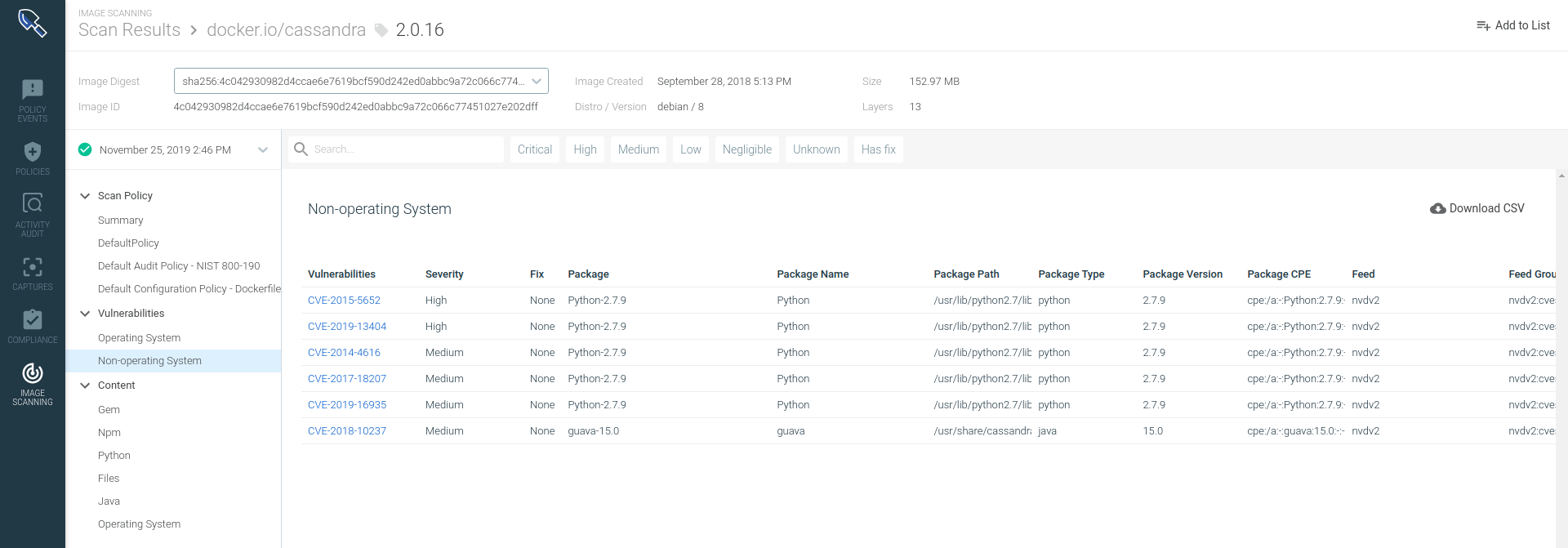
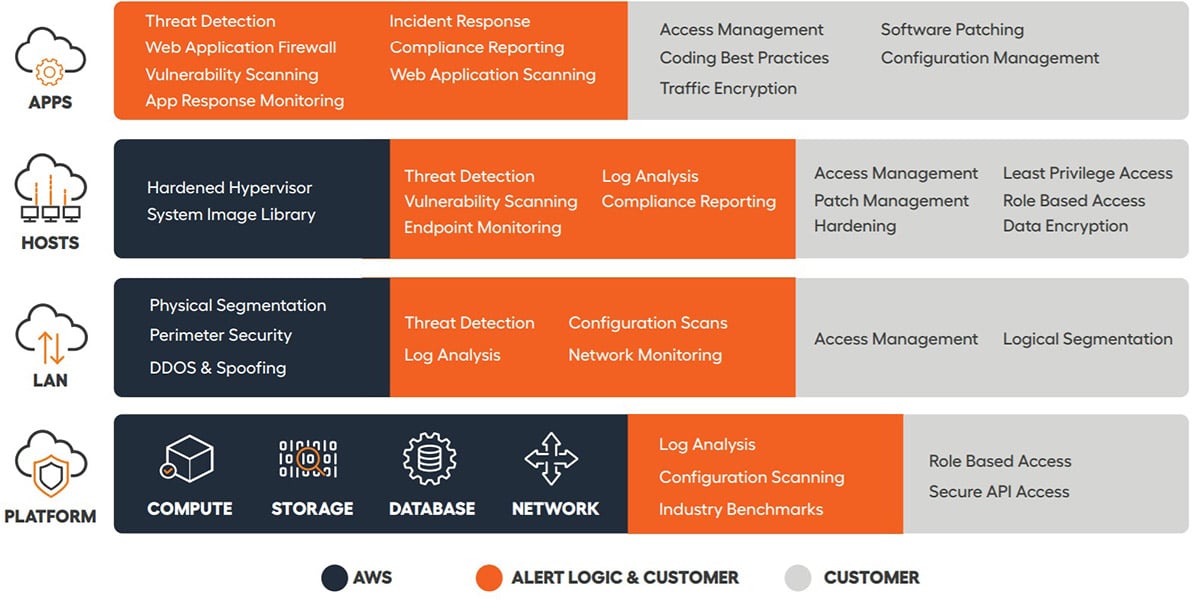
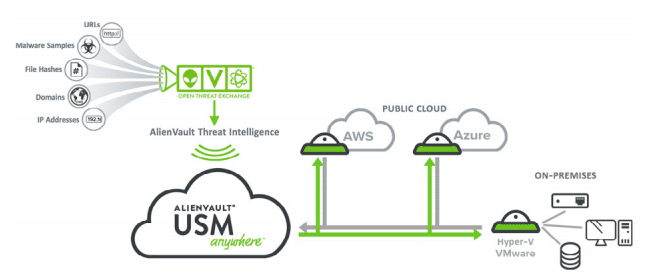
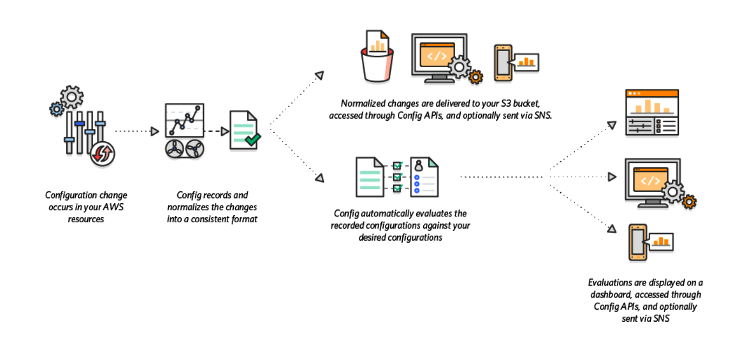
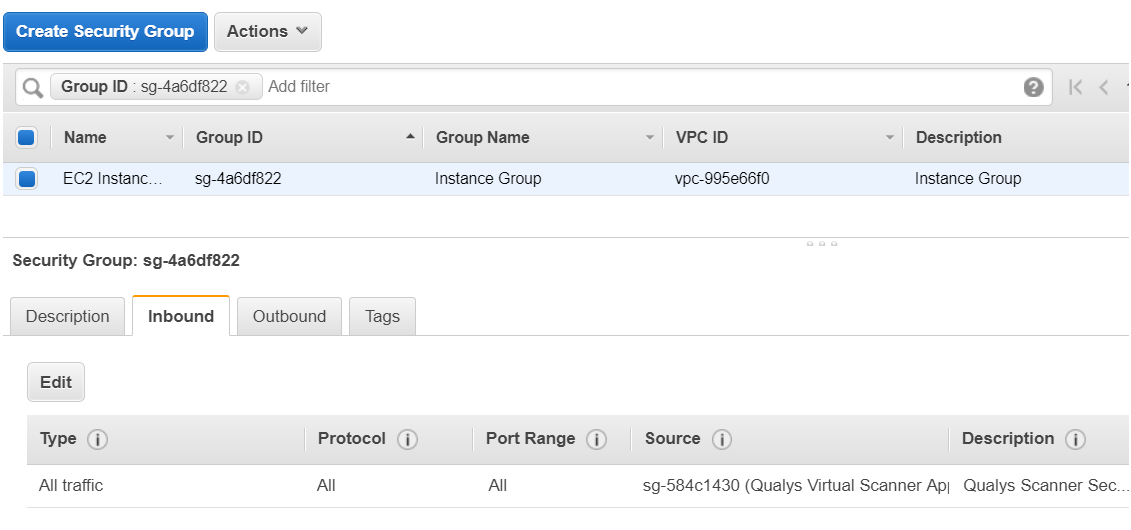
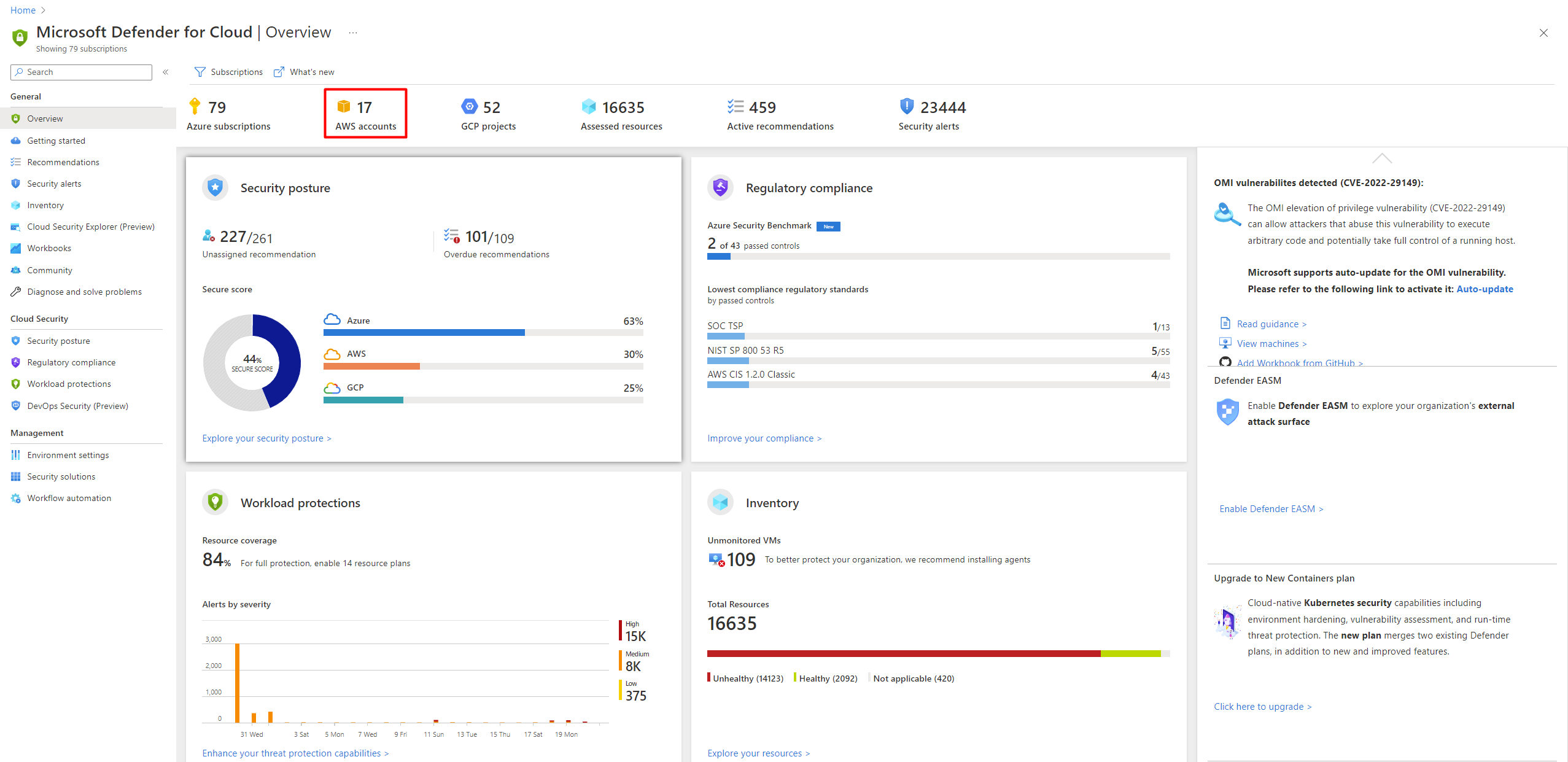
GitHub - toniblyx/my-arsenal-of-aws-security-tools: List of open source tools for AWS security: defensive, offensive, auditing, DFIR, etc.

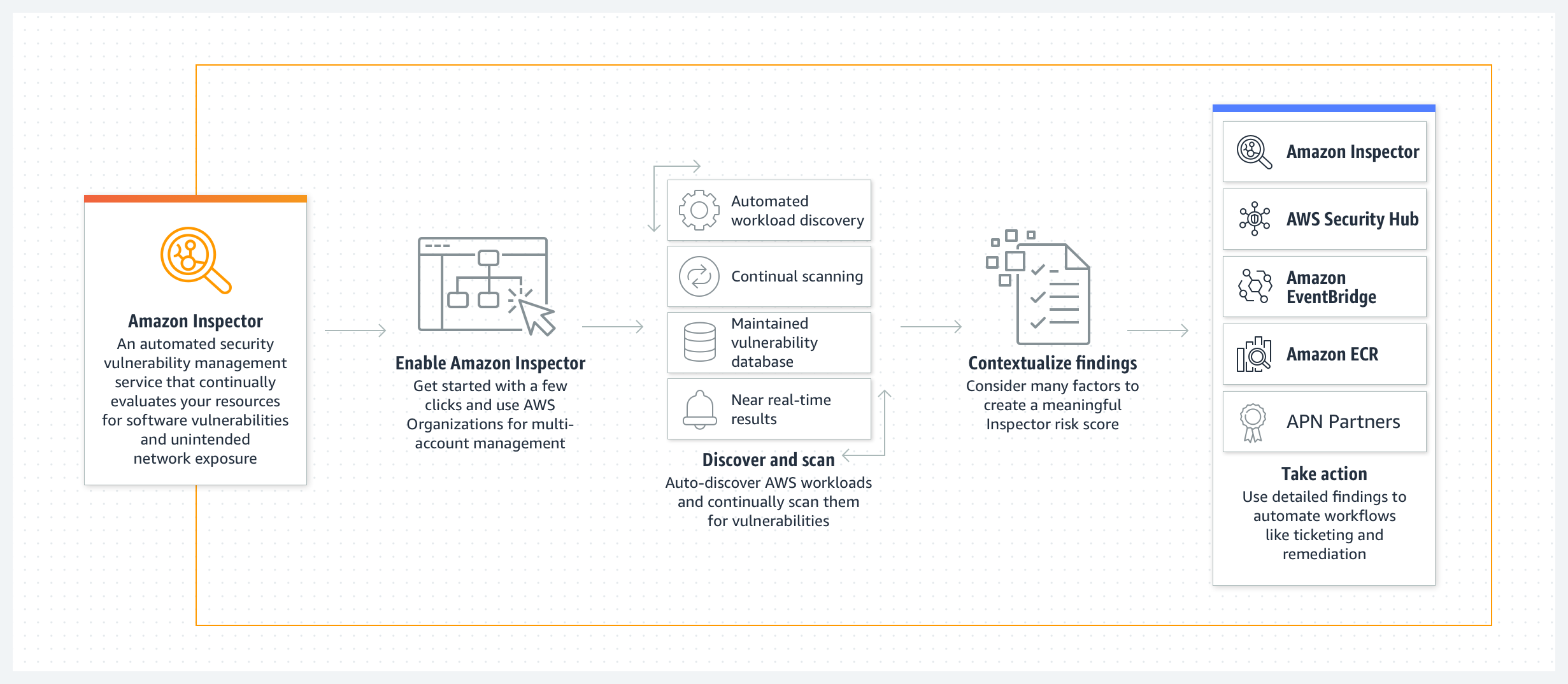
Improved, Automated Vulnerability Management for Cloud Workloads with a New Amazon Inspector | AWS News Blog

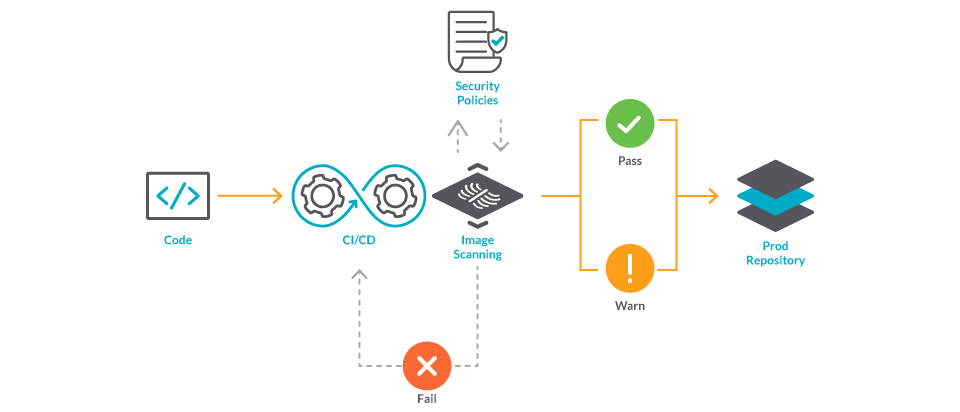
Integrating AWS CloudFormation security tests with AWS Security Hub and AWS CodeBuild reports | AWS Security Blog
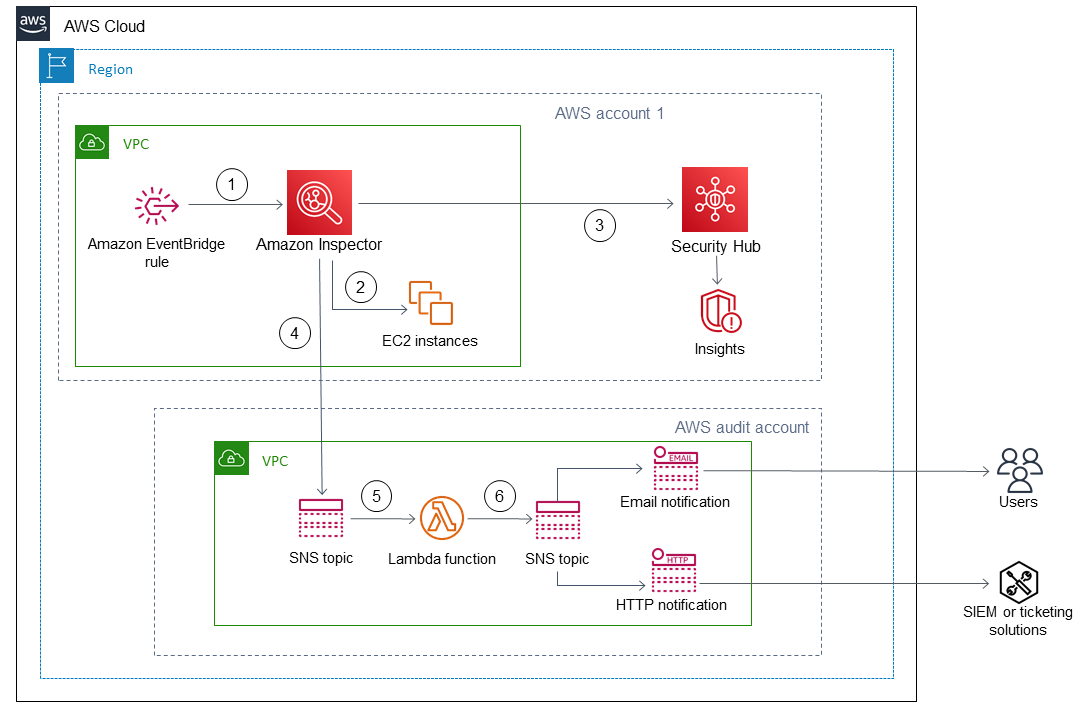
Automate security scans for cross-account workloads using Amazon Inspector and AWS Security Hub - AWS Prescriptive Guidance