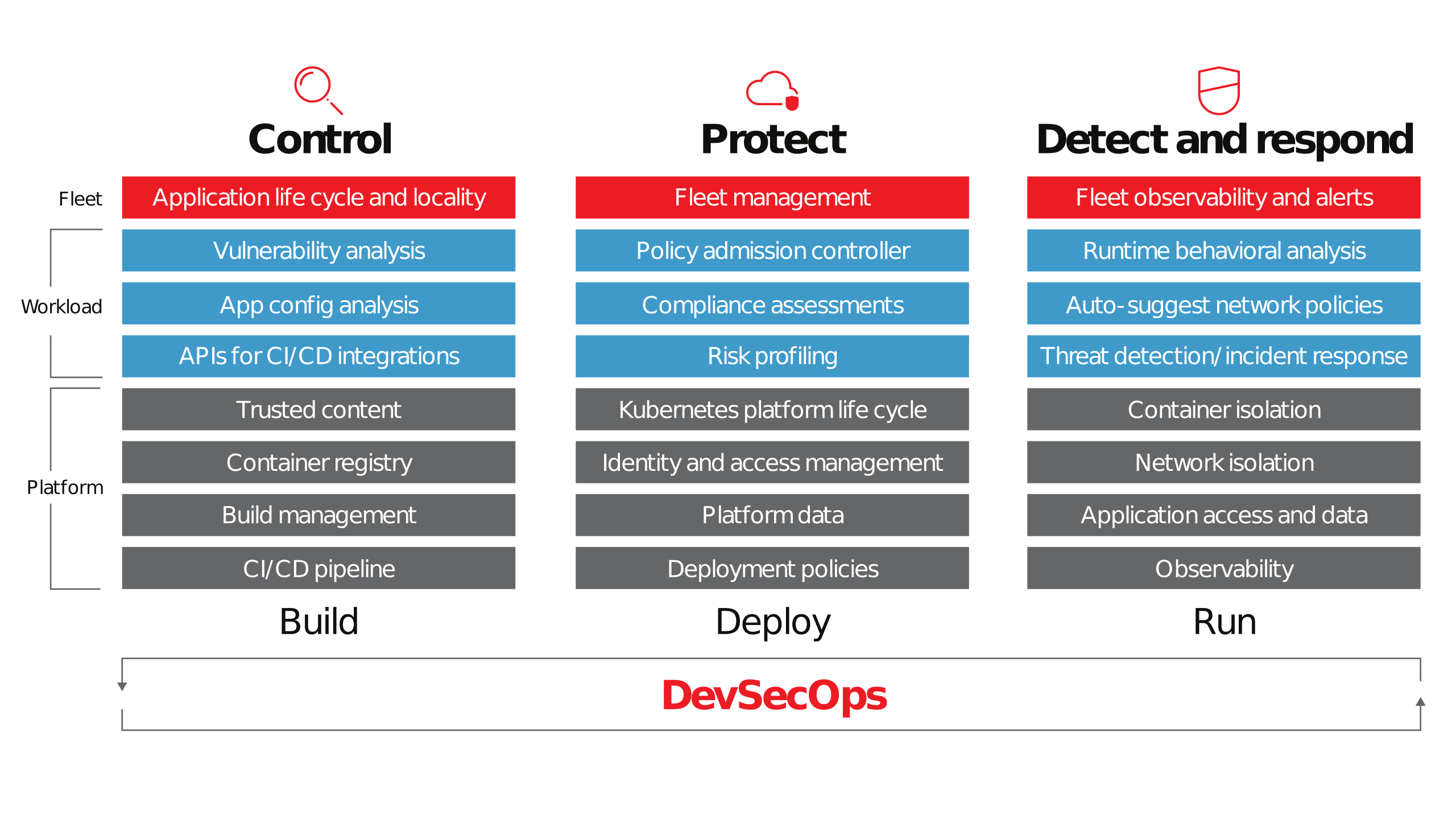
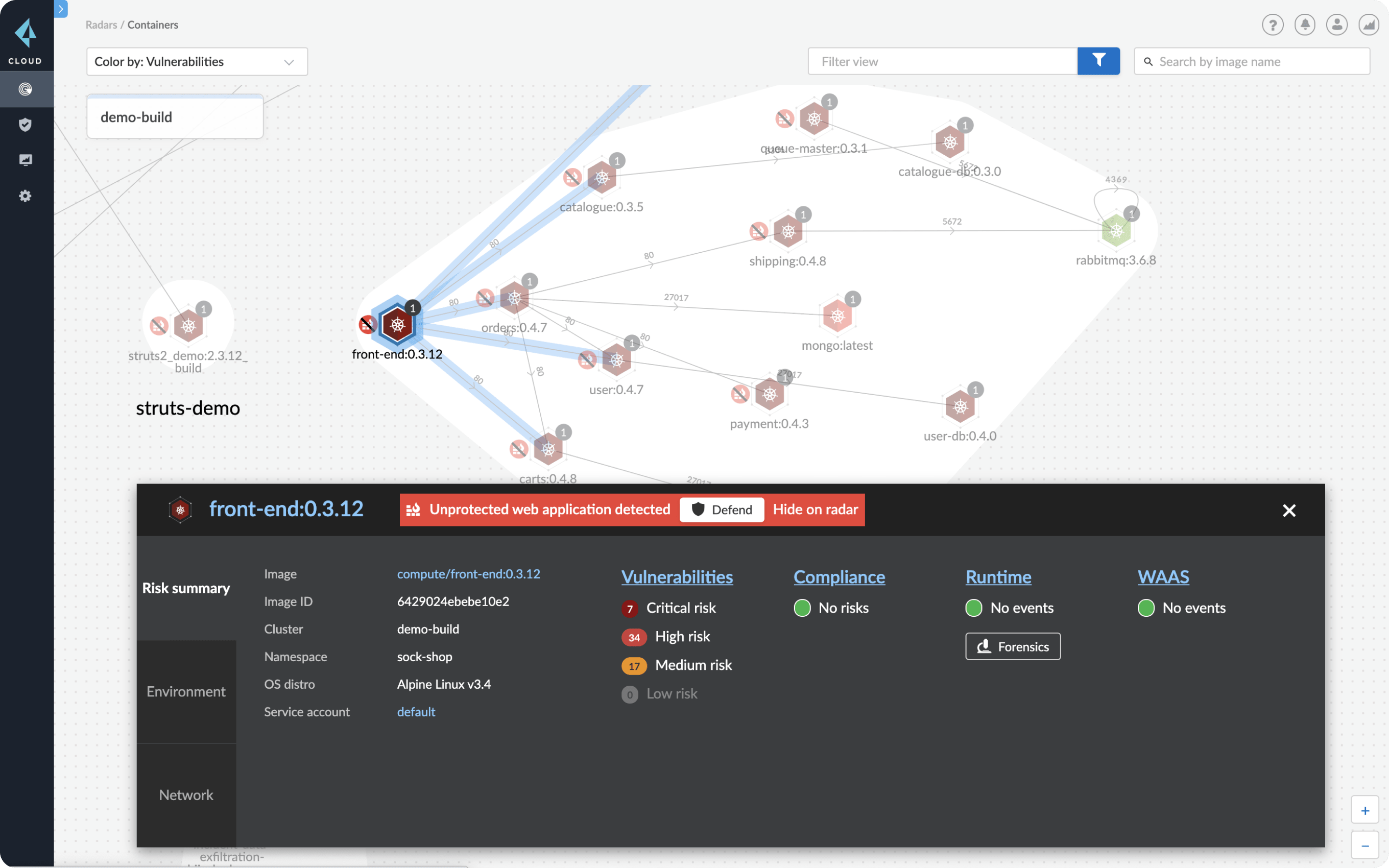
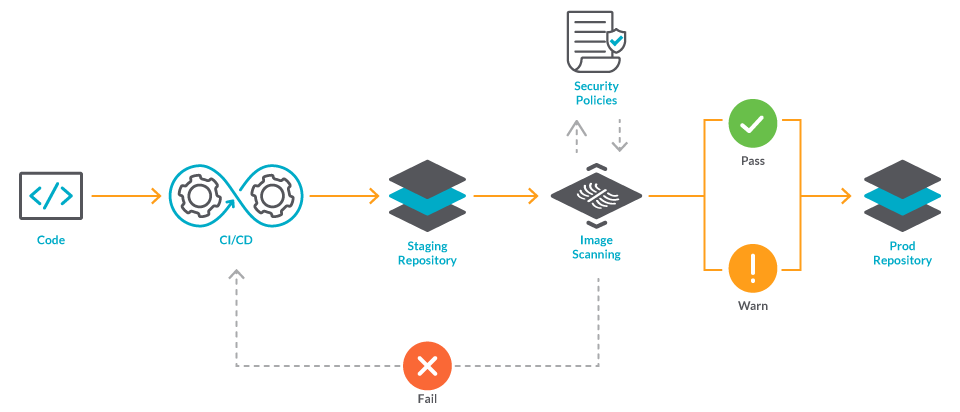
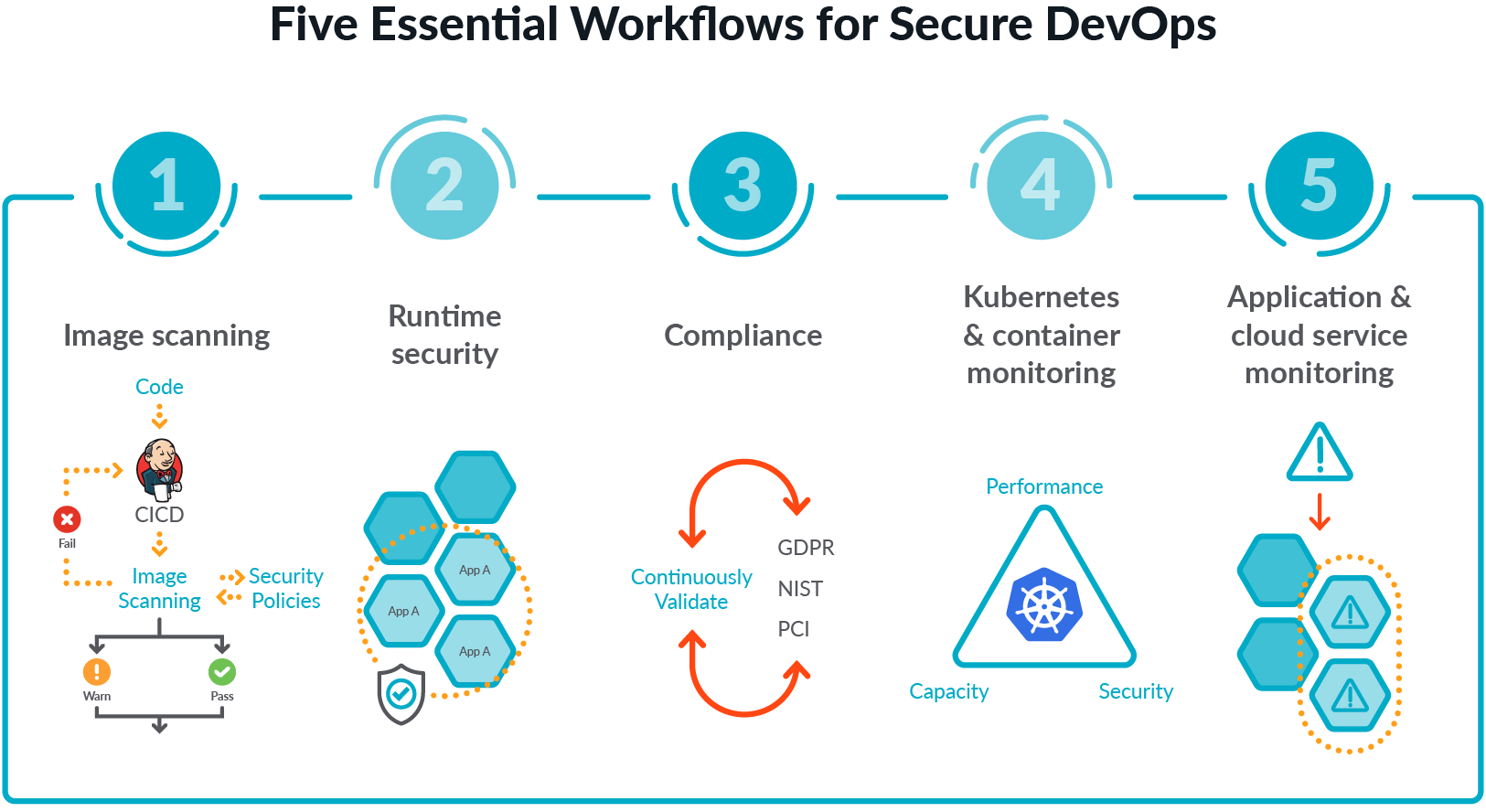
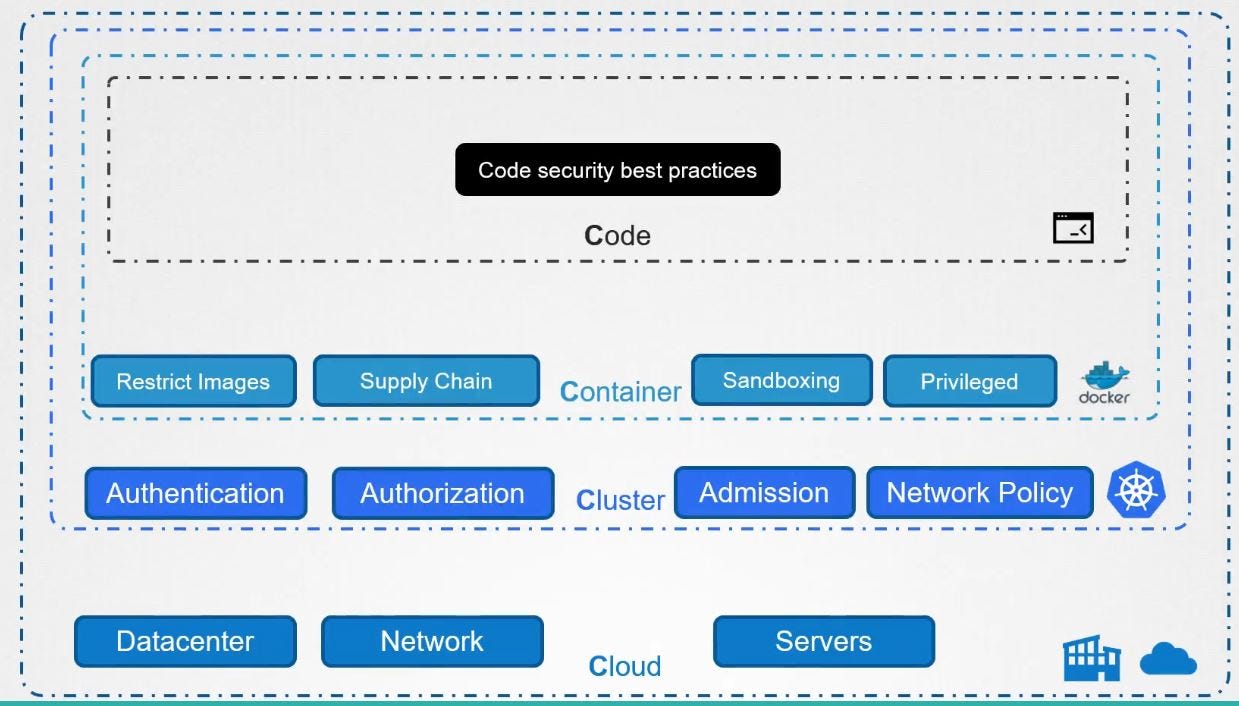
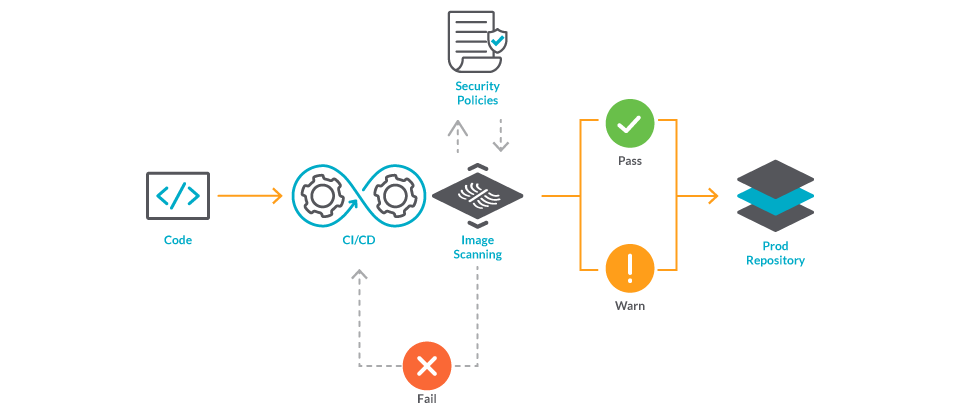
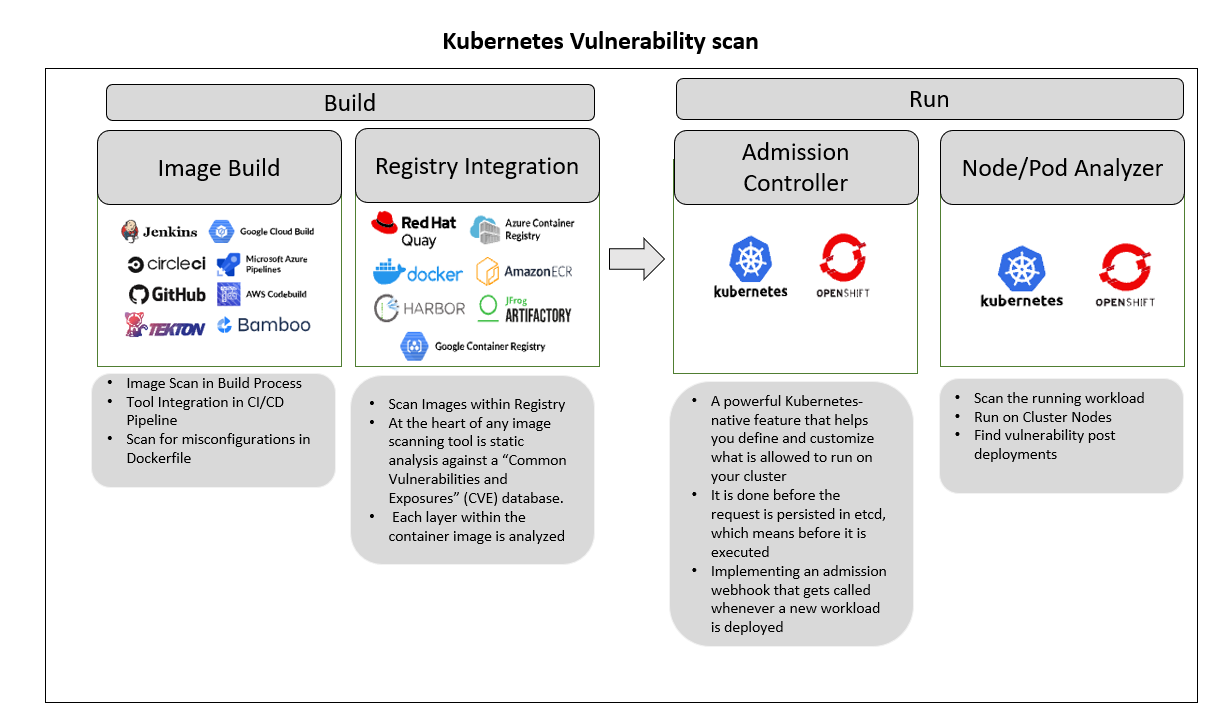
12 Scanners to Find Security Vulnerabilities and Misconfigurations in Kubernetes | by Walid El Sayed Aly | Towards Dev

Operator best practices - Container image management in Azure Kubernetes Services (AKS) - Azure Kubernetes Service | Microsoft Docs

Technical Report on Container Security (V)-3 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.
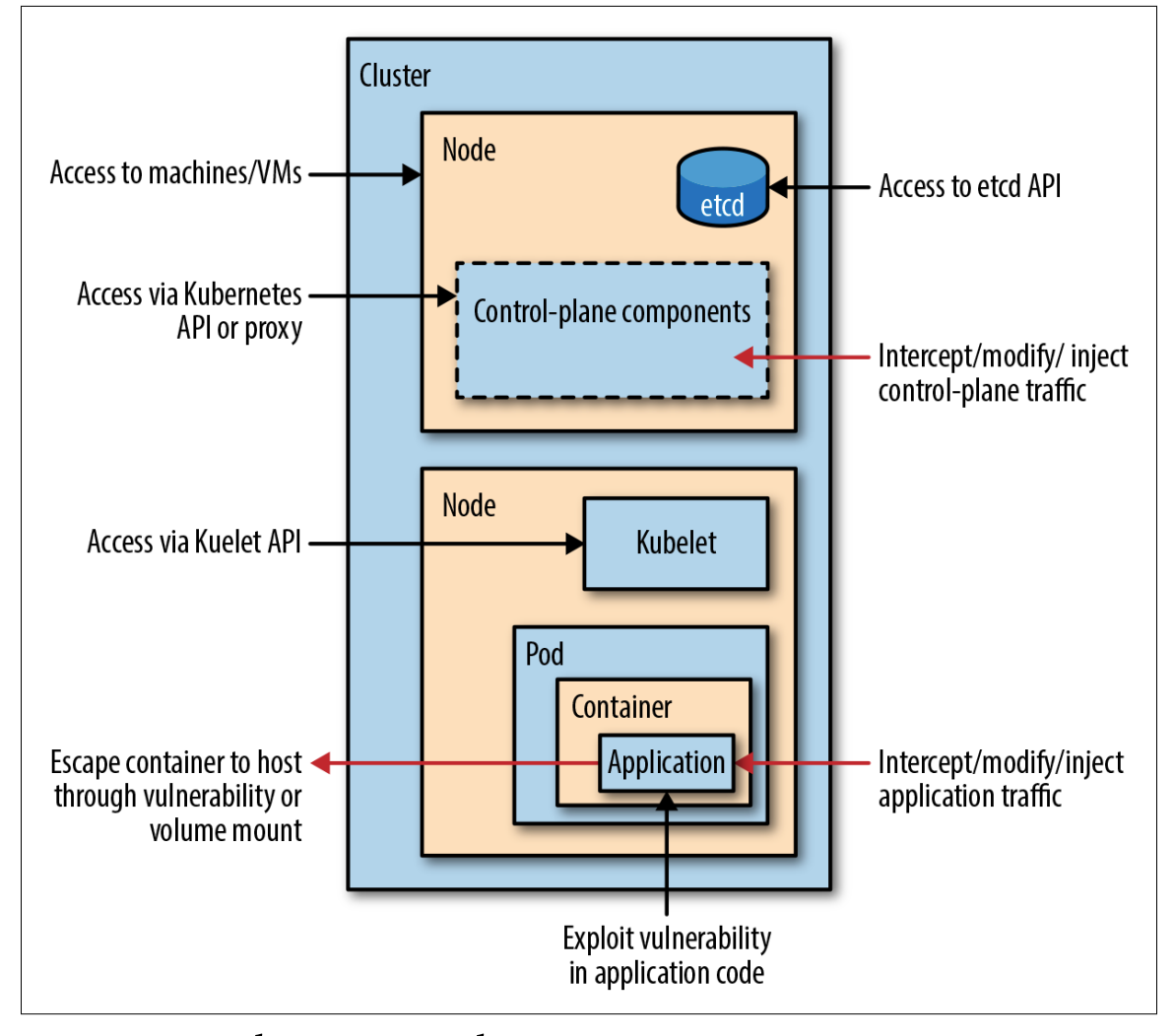
12 Scanners to Find Security Vulnerabilities and Misconfigurations in Kubernetes | by Walid El Sayed Aly | Towards Dev